Apple users: security is not for you
As of today, most Apple users are unable to access the HTTPS version of this web site while they can browse the unsecured version.
In order to allow my readers to privately use my site, I chose to equip it with a StartSSL one-year free certificate. To make it relatively safe against NSA and other agencies eavesdropping, I opted for a 4096 bit key size… except that my FFS (fat-finger syndrome) kicked in when I generated the certificate signature request, and my certificate has a 4906 bit [sic!] key size.
Because the key size is larger than 4096 bits or because it is not a power of two or a multiple of 512 bits, Chrome on OSX warns users that their connection may have been hijacked (thanks to Yann Pujante for the screenshot):
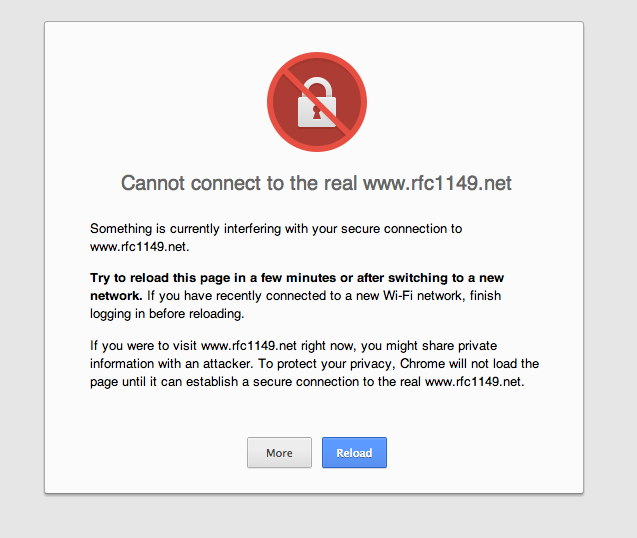
So, to summarize, a non-standard certificate size on my side makes OSX think that something fishy is happening: it does not flag the certificate as invalid, nor as unrecognized, but assumes that the connection to the server is being intercepted.
Some users have also attempted to access my secure website using Safari. One of them told me that the browser crashed, and another one that it displayed only a blank page. However, Firefox on OSX, which uses its own certificate validation, works just fine. As do other browsers, including Chrome, on GNU/Linux or Windows operating systems.
So it looks like the problem lies on Apple’s side. I attempted to renew my free certificate from StartSSL to make it more standard, but I have to wait until the previous one expires or to pay revocation fees. So unless an Apple user pays to get me a 4096 bit one-year SSL certificate (certificate signing request available on demand), they will have to wait for this one to be renewed in late August or for Apple to accept various or more secure keys. Which one will happen first?
And Google, you should also fix Chrome by not using OSX system libraries for certificate verification.